Cara Scan Serangan Csrf Di Acunetix
- Cara Scan Serangan Csrf Di Acunetix 2
- Cara Scan Serangan Csrf Di Acunetix 10
- Cara Scan Serangan Csrf Di Acunetix En
What Acunetix can do for you
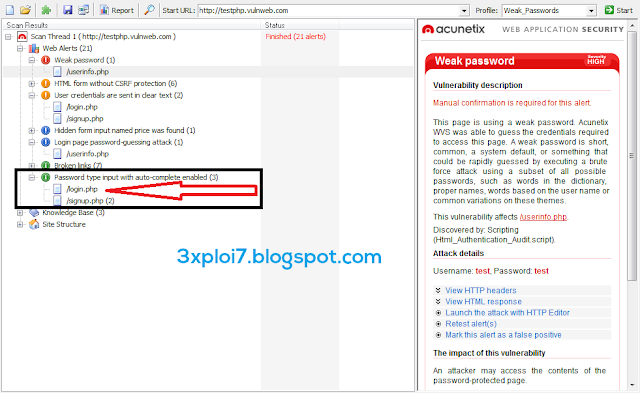
Pertama kali sebelum kita melakukan scanning Jangan sesekali melakukan scan website tanpa ada otorisasi. Website server akan mencatat semua scanning atau penyerangan apapun yang di lakukan oleh Acunetix WVS karena beberapa scan dapat menyebabkan situs tersebut mengalami kecelakaan dan membutuhkan restart dari situs web. Keamaan web memang sangat penting untuk menjamin kelangsungan website kita agar tetap online dan banyak di kunjungi oleh orang lain, namun tidak menutup kemungkinan website anda akan di susupi hacker atau orang-orang iseng alias lamer yang hanya sekedar test ilmu atau memang bermaksud jahat dengan cara-cara dan tingkat kemampuan yang mereka miliki.
Manage web and network security
Detect SQLi, XSS, and other issues
Umumnya para hacker mengambil alih website melalui beberapa cara seperti: Deface, SQL Injection, Malware, XSS, RFI, CRLF, CSRF, Base64 dsb. Berikut ini adalah beberapa trik pencegahan yang dapat anda upayakan untuk mengamankan website anda sebelum website kita menjadi korban hacker.
Find vulnerabilities in your websites and web APIs
- Highest detection rating of over 4500 vulnerabilities in custom, commercial, and open source apps with nearly 0% false positives.
- Acusensor (IAST) allows you to find and test hidden inputs not discovered during black-box scanning (DAST)
- Advanced Crawling & Authentication support gives you the ability to crawl Javascript websites and SPAs.
- Prioritize and classify detected issues to know how to invest your time
- Create management and compliance reports to find out what needs to be addressed
- Track fixed issues to know if they reappear and automatically retest to stay safe
Prevent hazards at the earliest stages of the SDLC
- Integrate with issue trackers such as Jira to streamline bug fixing processes
- Automate new build scanning – integrate with CI tools such as Jenkins
- Get detailed technical reports to understand and address identified vulnerabilities
It takes teamwork and collaboration to build and maintain an effective security program. Acunetix 360 allows you to easily set up workflows to help you address identified vulnerabilities. You can include security, development, and management teams in the process - any level of customization is possible. You may add as many users as you want with granular permissions, as well as use tools of choice such as email, Slack, text, and so on.
Automate with Acunetix“Acunetix has played a very important role in the identification and mitigation of web application vulnerabilities. Acunetix has proven itself and is worth the cost.
Thank you Acunetix team.”
“With Acunetix WVS we were able to perform our tasks better, thus improving the quality, stability and security of Joomla! We would like to thank Acunetix for supporting the Joomla! project and giving us the opportunity to use its tool.
Thank you Acunetix team.”
Cara Scan Serangan Csrf Di Acunetix 2
From the blog
Releases July 4, 2019
New build improves auto-login, detection of DOM XSS, WAFS, CDNs, and reverse proxies
The new Acunetix build improves Auto-Login, detection of DOM XSS, and crawling of Spring-based web applications. In addition, a number of vulnerability checks have been reviewed with the aim to further reduce the number of false positives.
Web Security Zone July 3, 2019
Billions of IoT User Records Leaked via an Unprotected Database
ORVIBO, a Chinese manufacturer of smart home devices, left an unprotected Elasticsearch database accessible online through a web interface with no authentication. The database contained more than 2 billion user records representing more than a million users of ORVIBO smart home devices worldwide.
Web Security Zone July 2, 2019
Insecure Default Password Hashing in CMSs
Researchers from the University of Piraeus checked default password hashing in open-source web platforms including the most popular content management systems (CMS) and web application frameworks. The results were very disappointing from the security point of view.
Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.
Knowledge Sharing
Popular Posts
In The News
'We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.'
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, XeroxRead more case studies >Take action and discover your vulnerabilities
Cara Scan Serangan Csrf Di Acunetix 10
Cara Scan Serangan Csrf Di Acunetix En
Get Demo- This alert requires manual confirmation
Cross-Site Request Forgery (CSRF, or XSRF) is a vulnerability wherein an attacker tricks a victim into making a request the victim did not intend to make. Therefore, with CSRF, an attacker abuses the trust a web application has with a victim's browser.
Acunetix found an HTML form with no apparent anti-CSRF protection implemented. Consult the 'Attack details' section for more information about the affected HTML form.
- Verify if this form requires anti-CSRF protection and implement CSRF countermeasures if necessary.
The recommended and the most widely used technique for preventing CSRF attacks is know as an anti-CSRF token, also sometimes referred to as a synchronizer token. The characteristics of a well designed anti-CSRF system involve the following attributes.- The anti-CSRF token should be unique for each user session
- The session should automatically expire after a suitable amount of time
- The anti-CSRF token should be a cryptographically random value of significant length
- The anti-CSRF token should be cryptographically secure, that is, generated by a strong Pseudo-Random Number Generator (PRNG) algorithm
- The anti-CSRF token is added as a hidden field for forms, or within URLs (only necessary if GET requests cause state changes, that is, GET requests are not idempotent)
- The server should reject the requested action if the anti-CSRF token fails validation
When a user submits a form or makes some other authenticated request that requires a Cookie, the anti-CSRF token should be included in the request. Then, the web application will then verify the existence and correctness of this token before processing the request. If the token is missing or incorrect, the request can be rejected.